MANRS in the news: Oracle ‘net-watcher agrees, China Telecom is a repeat offender for misdirecting traffic
Network admins really need to mind their MANRS
In other words, having let their systems accept the route announcements, network admins failed to correct the error for up to two-and-a-half years.
Madory told The Register: “BGP routes from Verizon APAC were partially routed through China Telecom beginning in December 2015 and going until April 2018 (~2.5 years). Those routes should never have gone through China Telecom for anywhere except in China.”
Verizon APAC errors had a knock-on effect, he explained: “Verizon APAC … were announcing [routes] to the internet on behalf of their customers. A couple of AS hops away, China Telecom was mishandling them – announcing them in a manner that would cause internet traffic destined for those IP address ranges to flow back through China Telecom’s network.”
Verizon APAC was involved in another erroneous announcement, and in his blog post, Madory wrote: “When these routes were in circulation, networks peering with China Telecom (including those in the US) accepted AS701 routes via AS4134, sending US-to-US traffic via mainland China. One of our affected clients was a major US internet infrastructure company.”
While path monitoring can help prevent leaks, it’s not a complete solution because leaks can occur “multiple hops from the origin”.
“Verizon APAC (AS703) likely established a settlement-free peering relationship with SK Broadband (AS9318), unaware that AS9318 would then send Verizon’s routes exclusively on to China Telecom and who would in turn send them on to the global internet,” Madory said.
Networks also need to watch the announcements they receive from their peers, which Madory noted is rare, and he directed his readers to the Internet Society’s MANRS project. ®
Bootnote
Madory’s post is a welcome corroboration of the Demchack/Shavit paper, even without addressing the question of intent.
China has been accused of BGP hijacks in the past – for example, in 2010, when tainted tables twice redirected as many as 37,000 networks to China Telecom.
However, BGP hijacks are almost routine. At the time of writing, BGPStream reported 18 BGP advertisements as “possible hijacks” for the few first days of November alone.
Some of these are already going on a bit – there’s currently a mixup between Harmony Hosting and France’s internet exchange GIXE that’s lasted more than 100 hours.
Whether malicious or accidental, China Telecom’s repeated BGP errors mean providers should handle its route announcements with care – and, as Madory wrote, the more networks that join the MANRS initiative, the better.
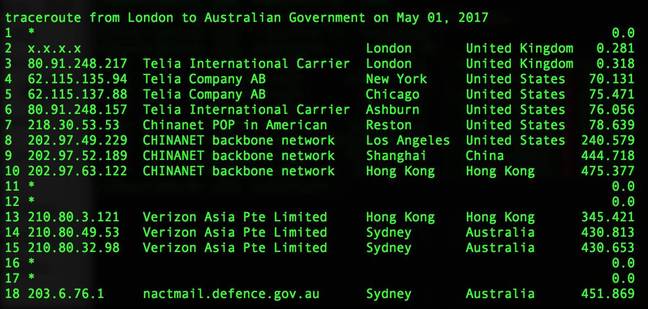 The long way home … London to Sydney via China
The long way home … London to Sydney via China
Leave a Comment