Public DNS in Taiwan the latest victim to BGP hijack
Yet another incident of Border Gateway Protocol (BGP) hijack, with the latest victim this time in Taiwan. Earlier this month (May 8), traffic going through a public DNS run by Taiwan Network Information Center (TWNIC) rerouted to an entity in Brazil for about three and a half minutes.
It remains to be investigated whether the route hijacking was malicious or inadvertent, but for something as important as a backbone of the Internet, even a three-and-a-half-minute leak was too great a risk, and unimaginable damage could have been done.
Similar incidents can happen again at any time anywhere in the world, and network operators have a responsibility to ensure a globally robust and secure routing infrastructure. Yet, a lot more must be done by network operators to heighten routing security.
What Happened?
Quad101 is an experimental Public DNS project, branded a privacy-centric DNS resolver run by TWNIC, a ccTLD (country-code Top Level Domain) registry operator. TWNIC runs one of the world’s fastest DNS infrastructure, according to Quad 101’s website.
The specific IP address (101.101.101.101) has been assigned to Quad101 Public DNS systems.
On May 8, at around 15:08 UTC an entity in Brazil (AS268869) started advertising 101.101.101.0/24 which does not belong to them. It was an attempt to hijack the Quad101 prefix.
aut-num: AS268869
owner: FIBRA PLUS TELECOMUNICA??ES LTDA EPP
responsible: ANDERSON LUCAS GALLACCI
owner-c: FPTLE1
routing-c: FPTLE1
abuse-c: FPTLE1
created: 20190412
changed: 20190412
inetnum: 45.174.220.0/22
inetnum: 2804:5bc8::/32
Route dump from isolario.it project captured the first announcement at 15:08:55 on May 8.
+|101.101.101.0/24|199036 28329 3549 4230 4230 4230 4230 268869|82.94.230.130|?|||3549:602 3549:2162 3549:34076 28329:2111 28329:2900 28329:12100|82.94.230.130 199036 112|1557328135|1
Whereas RIPE RIS received first announcement from AS268869 at 08.05.2019 15:08:39.
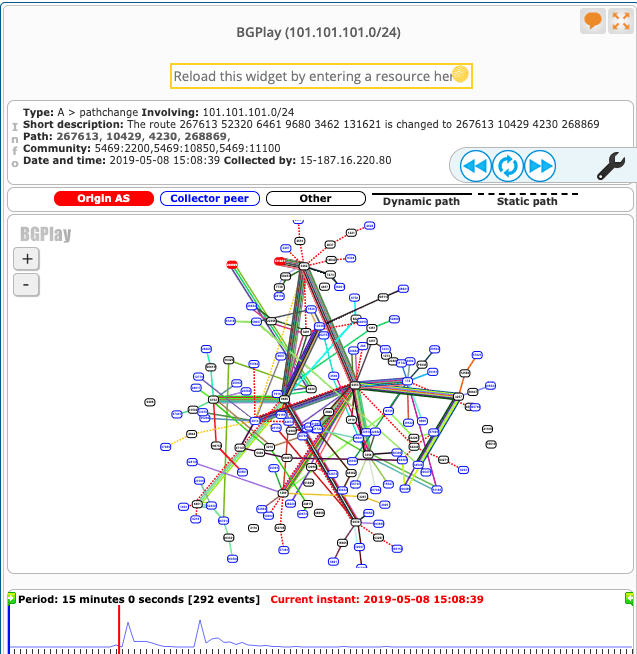
Last announcement recorded by isolario.it from AS268869 was at 15:12:15.
+|101.101.101.0/24|199036 198644 5603 3320 2828 4230 268869|82.94.230.130|82.94.230.130 199036 68|1557328335|1
And as per RIPE RIS the last announcement received at 15:11:42.
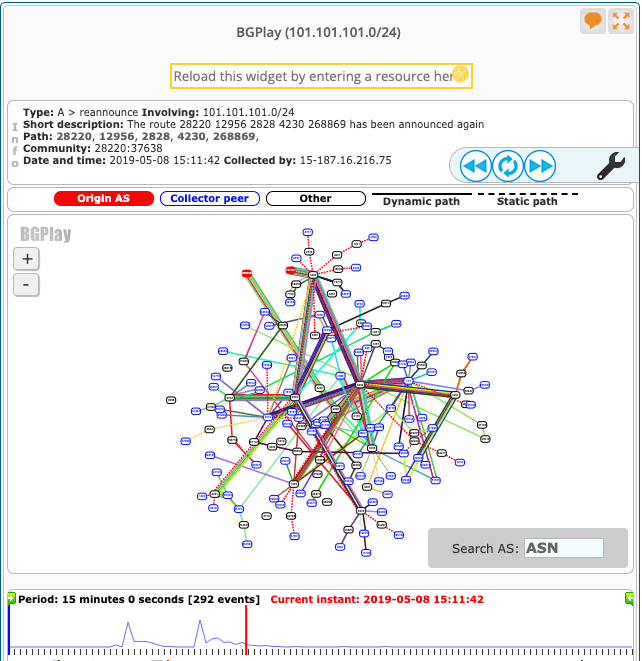
So how did that happen? If you look at the announcements from AS268869 within the same time window, there were 2 IPv4 prefixes which do not belong to them i.e. 101.101.101.0/24 and 102.102.102.0/24. This could be a classic example of testing something in the network and inadvertently leaking it to the Internet, but it could also be an attempt to hijack a Public DNS and using 102.102.102.0/24 as a decoy.
This shouldn’t have happened if AS268869 implemented the BCP 194 (RFC7454 – BGP Operations and Security) and filtered outbound prefixes. But this is not only the mistake of AS268869 because they are connected to AS4230 – Claro Brasil who propagated these bogus announcements to the global routing table. AS4230 didn’t apply any prefix filters while receiving it from AS268869 and they didn’t apply any checks (through IRR entries) while propagating these hijacked prefixes.
What Do We Do About It?
Network operators have a responsibility to ensure a globally robust and secure routing infrastructure. No operator can secure their own network entirely by themselves. Routing security depends on the actions of other networks, and every network should help secure the global routing system as a whole.
That’s where the Mutually Agreed Norms for Routing Security (MANRS) comes in. MANRS is a community initiative of network operators and Internet Exchange Points (IXPs) that creates a baseline of security expectations for routing security. MANRS calls for simple, but concrete actions that will reduce the most common routing threats, including BGP hijacking.
The first MANRS action is filtering, which prevents the propagation of incorrect routing information. If most network operators and IXPs implement the MANRS actions – including filtering – BGP hijacking events would not propagate across the Internet, and we could avoid outages, traffic inspection, and DoS attacks.
Other MANRS actions include anti-spoofing, global validation, coordination, MANRS promotion, and monitoring and debugging tools.
How Do I Get Started?
- Read about the MANRS actions for network operators and/or the MANRS actions for IXPs.
- Take the six MANRS tutorials to learn about how to implement the actions. This module on filtering is particularly relevant to BGP hijacking.
- Implement the appropriate actions for your network.
- Join the MANRS community of security-minded organizations working to raise the bar on routing security.
Leave a Comment